Azure Update Manager provides a built-in SaaS experience to manage and govern software updates across your Windows and Linux machines, whether they run in Azure, on-premises, or multi-cloud environments. Building on top of the core functionality of Azure Automation Update management, it gives you new features that let you more easily assess and deploy software updates if you manage just one machine or hundreds at scale.
Key Benefits and Enhancements
Centralized Update Compliance
- Scope: From a single interface, you can manage updates for Azure VMs, on-premises machines, and multi-cloud environments, including Arc-enabled Servers.
- Efficiency: Keep track of update compliance across all your machines to ensure they’re secure and up to date.
Instant Deployment of Updates
- Visibility: Instantly view and deploy pending updates to secure your machines without any delays.
- Consistency: Enjoy a consistent update deployment experience, including support for extended security updates (ESUs) on Azure Arc-enabled Windows Server 2012/2012 R2 machines.
Flexible Update Scheduling
- Recurring Time Windows: Set up recurring time windows for updates and reboots, ensuring maintenance happens without disrupting your operations.
- Dynamic Scoping: Use dynamic scoping based on Azure constructs to enforce common patch schedules for grouped machines.
- Sync with Patch Tuesday: Align your patch schedules with Microsoft’s Patch Tuesday for consistent security updates.
Efficient Update Rollouts
- Incremental Rollout: Roll out updates incrementally to Azure VMs during off-peak hours to minimize disruptions.
- Reduced Reboots: Minimize reboot frequency by enabling hot patching for eligible updates, reducing downtime.
Automated Assessment and Compliance
- Periodic Assessments: Automatically assess machines for pending updates every 24 hours and flag non-compliant machines.
- Scalable Enforcement: Enforce periodic assessments on multiple machines at scale using Azure Policy.
Custom Reporting
- Insightful Analysis: Create custom reports to gain deeper insights into update data and trends within your environment.
Granular Access Management
- Security: Implement granular access controls using Azure roles and identity, ensuring only authorized users can perform update operations and edit schedules.
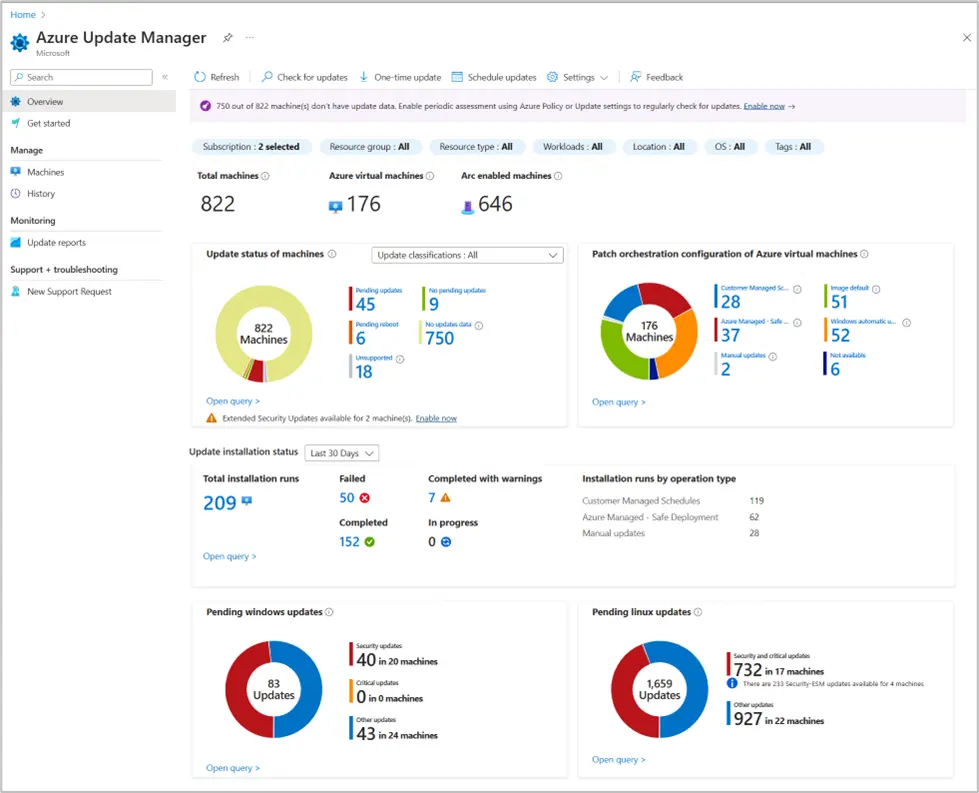
To help you manage your Azure VMs or other machines, Update Manager uses a special Azure extension. This extension does all the necessary work to interact with the operating system and handle updates. It gets automatically installed when you start any Update Manager tasks, like checking for updates or installing them.
This extension works smoothly with Azure VMs and Azure Arc-enabled servers. For Azure VMs, it’s managed through the Azure VM Windows agent or Azure VM Linux agent. For non-Azure machines or physical servers, it’s managed through the Azure Arc-enabled servers agent.
You don’t need to worry about installing or setting up the extension yourself. Update Manager takes care of that for you. As long as the Azure VM agent or Azure Arc-enabled server agent is working, everything runs smoothly.
The extension does a few key things:
- It checks the status of system updates through the Windows Update client or Linux package manager.
- It downloads and installs approved updates using the Windows Update client or Linux package manager.
In Azure Update Manager, you have various update options and orchestration features to ensure your systems are up to date and secure.
Update Options:
- One-Time Update:
- Allows you to install a specific update or set of updates on-demand.
- Useful for addressing immediate security concerns or applying critical patches.
- Scheduled Patching:
- Enables you to define recurring time windows during which your machines receive updates.
- Helps in maintaining a predictable maintenance schedule without disrupting operations.
- You can sync patch schedules with Microsoft’s Patch Tuesday releases for Windows machines.
- Automatic VM Guest Patching:
- Facilitates incremental rollout of updates to Azure VMs during off-peak hours.
- Reduces the need for manual intervention and minimizes disruption by automatically applying updates.
Orchestration Features:
- Dynamic Scoping:
- Allows you to group machines together based on Azure constructs like Subscription, Location, Resource Group, Tags, etc.
- Ensures that machines with similar characteristics have common patch schedules.
- Enhances manageability and scalability by applying updates to multiple machines at once.
- Granular Access Management:
- Enables you to control who can perform update operations and edit schedules using Azure roles and identity.
- Ensures security by restricting access to update-related tasks to authorized personnel only.
- Automated Assessment and Compliance:
- Automatically assesses machines for pending updates every 24 hours.
- Flags machines that are out of compliance, making it easier to identify and address update-related issues.
- Enforces periodic assessments on multiple machines at scale using Azure Policy.
Customization and Reporting:
- Custom Reports:
- Allows you to create custom reports for deeper understanding of update data within your environment.
- Provides insights into update trends, compliance status, and more.
- Extended Security Updates (ESUs):
- Manages ESUs for Azure Arc-enabled Windows Server 2012/2012 R2 machines.
- Provides a consistent experience for the deployment of ESUs and other updates.
Overall Benefits:
- Simplifies update management across Azure VMs, on-premises, and multi-cloud environments.
- Enhances security by ensuring timely application of updates and patches.
- Streamlines update processes, reducing manual intervention and minimizing disruption to operations.
If you’re in need of a cloud-based update manager for your organization, please feel free to contact us.

